Introduction:
Welcome to the beginning of an exciting networking series where I'll be sharing all the basic networking knowledge that I've acquired throughout my journey. Networking is a vast and essential field that underlies the connectivity we experience in our modern digital world. In this first part, we'll dive into the foundational concepts and technologies that form the backbone of networking. So, let's get started!
Understanding Networking:
Networking is the process of connecting computers, devices, and systems to enable communication and information sharing.
It involves creating a network, which acts as a pathway for data to travel between devices, allowing them to exchange information.
Networks can be wired or wireless. Wired networks use physical cables to connect devices, while wireless networks transmit data using radio waves without the need for cables.
Networking enables devices to share resources such as files, printers, and internet connections, making it easier for multiple users to access and utilize the same resources simultaneously.
The internet itself is a vast network of networks, connecting millions of devices worldwide. By connecting to the internet, users can access websites, services, and information from anywhere in the world.
Networking plays a crucial role in enabling communication and collaboration between individuals, organizations, and systems, facilitating the flow of information and enhancing productivity.
The Internet
The Internet is a global network: The Internet is a massive network that connects millions of computers, devices, and networks around the world.
Interconnected networks: The internet is made up of interconnected networks. These networks can be local networks within homes, offices, or institutions, or they can be larger networks operated by Internet service providers (ISPs).
Communication through protocols: The Internet relies on a set of protocols called the Internet Protocol Suite (TCP/IP) to enable communication between devices. These protocols define how data is transmitted, routed, and received across the internet.
Data packets: When you send or receive information over the internet, it is broken down into smaller units called data packets. These packets contain the data being transmitted, along with addressing information that helps them reach their intended destination.
Routing data packets: Data packets travel through various routers across the internet to reach their destination. Routers are devices that analyze the addressing information in the packets and determine the best path for them to reach their destination efficiently.
IP addresses: Every device connected to the internet, whether it's a computer, smartphone, or any other device, is assigned a unique identifier called an IP address. IP addresses are numerical values that serve as the "address" of a device on the internet, allowing it to send and receive data.
Domain names and DNS: Instead of using IP addresses directly, we often use domain names to access websites or services on the internet. Domain names, like example.com, are easier to remember. The Domain Name System (DNS) translates domain names into their corresponding IP addresses so that data can be routed correctly.
Internet Service Providers (ISPs): ISPs are companies that provide individuals and organizations with access to the Internet. They connect their customers to the internet through various technologies like fiber-optic cables, DSL, cable, or satellite connections.
Data Packets

Data packets are like small envelopes that hold pieces of information.
They are used to send data over networks, like the Internet, from one place to another.
Each packet has two parts: a header and a payload.
The header contains information about where the packet is coming from and where it's going.
The payload is the actual data being sent, like a message, a picture, or a video.
Data packets are sent separately and can take different paths to reach their destination.
This helps make the transmission faster and more reliable.
When the packets arrive at their destination, they are put back together to form the original data.
If a packet gets lost or damaged along the way, the network can send it again.
Using data packets allows for efficient and secure communication between computers, phones, and other devices connected to a network.
Routers

Routing Function: Routers are devices that perform the crucial function of directing network traffic between different networks.
Network Connection: Routers connect multiple networks, enabling devices from different networks to communicate with each other.
Packet Forwarding: When a device sends data across a network, the data is divided into smaller units called packets. Routers examine the packets' destination addresses and determine the most efficient path to forward them.
Path Determination: Routers use routing tables to determine the best path for forwarding packets. These tables contain information about network addresses and corresponding routes.
Network Address Translation (NAT): Routers can perform NAT, which allows multiple devices on a local network to share a single public IP address when communicating with the internet. NAT enhances security and conserves IP addresses.
Firewall Functionality: Many routers include firewall capabilities, which provide an additional layer of security by filtering incoming and outgoing network traffic based on predefined rules.
Wireless Access Point: Some routers also function as wireless access points, allowing devices to connect to the network wirelessly through Wi-Fi.
Switches

Local Network Connectivity: Switches are devices used to connect multiple devices within a local network, such as a home, office, or school.
Packet Switching: Switches operate at the data link layer of the networking model and forward data packets to their intended recipients within the local network.
MAC Address Learning: Switches learn and store the Media Access Control (MAC) addresses of connected devices. This knowledge allows switches to direct packets specifically to the intended recipients, improving network efficiency.
Broadcast and Multicast Filtering: Switches prevent unnecessary network congestion by selectively forwarding broadcast and multicast traffic only to the relevant devices within the local network.
Hub

A hub in networking refers to a basic networking device that connects multiple devices in a local area network (LAN) by forwarding data packets between them.
Physical Layer Device: Hubs operate at the physical layer (Layer 1) of the OSI model. They are responsible for providing a central point of connectivity for network devices.
Broadcast Communication: When a hub receives a packet of data, it broadcasts it to all connected devices in the network, regardless of the intended destination. This is known as "broadcast communication" and can lead to inefficient use of network bandwidth.
Simple and Unintelligent: Hubs are simple devices without any advanced features or intelligence. They lack the ability to analyze, filter, or manage network traffic. They simply receive incoming packets and forward them to all connected devices.
Collision Domains: Hubs create a single collision domain, meaning that when two devices connected to a hub transmit data simultaneously, a collision occurs. Collisions can degrade network performance and lead to packet loss.
Shared Bandwidth: All devices connected to a hub share the available bandwidth. If multiple devices are actively transmitting data, the overall network performance may be negatively affected due to congestion.
Limited Scalability: Hubs have a limited number of ports available for device connections. Once all the ports are occupied, additional devices cannot be directly connected unless a separate hub or switch is added.
Outdated Technology: Hubs have become outdated in modern networking. They have been largely replaced by switches, which offer better performance, enhanced features, and more efficient data transmission.
Signal Regeneration: One advantage of hubs is their ability to regenerate weak signals. If a signal weakens over long cable distances, a hub can amplify and regenerate it to maintain signal strength.
Cost-Effective: Hubs were popular in early networking due to their low cost compared to switches. However, as switch prices have decreased over time, hubs have become less prevalent in modern network infrastructures.
Hub vs. Switch: While hubs broadcast data to all connected devices, switches intelligently forward data packets only to the intended recipient. Switches analyze the destination MAC addresses, reducing unnecessary network traffic and improving performance.
Remember, hubs are an older networking technology and have largely been replaced by switches due to their limitations.
LAN (Local Area Network)
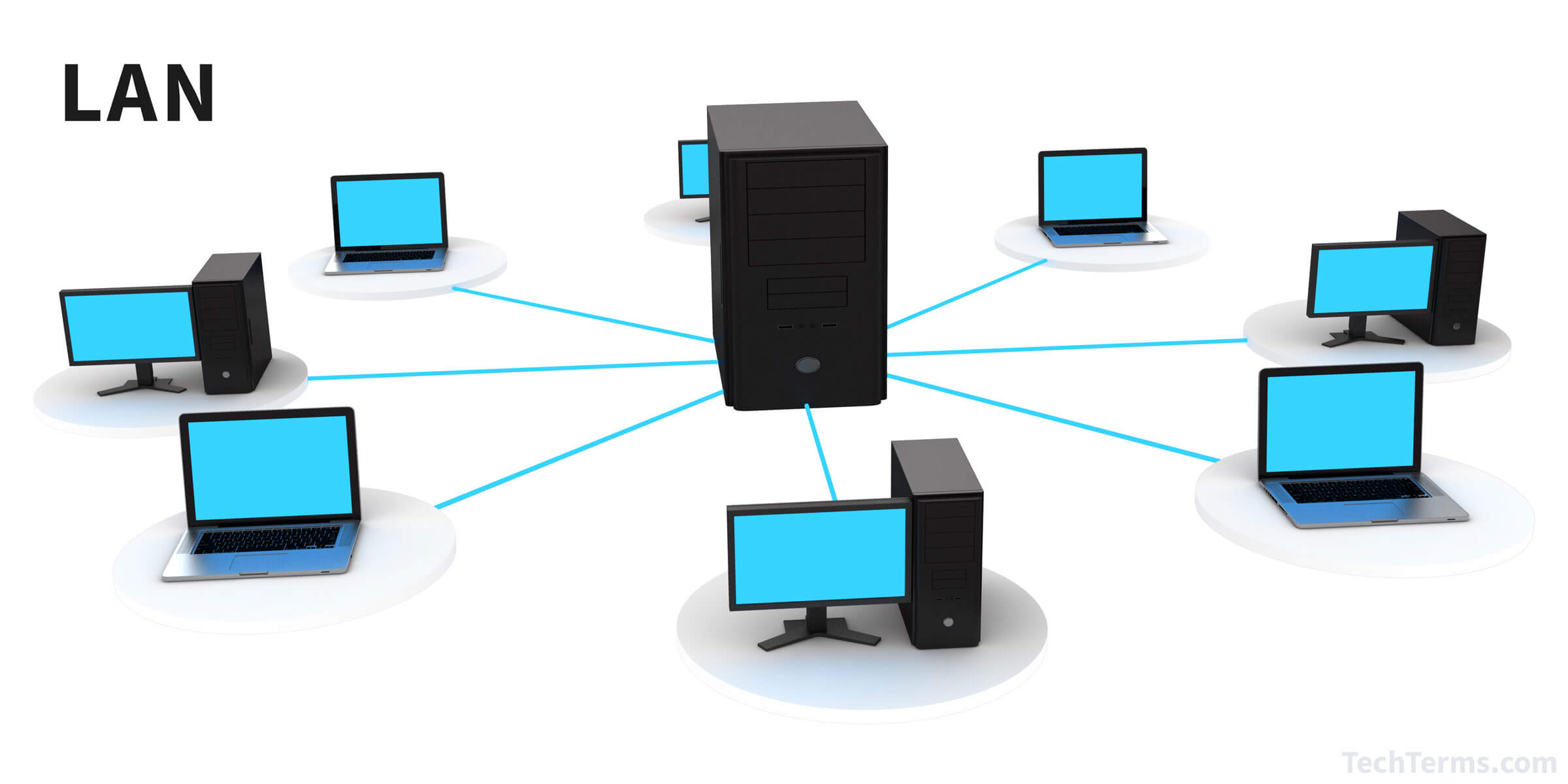
Local Network: A LAN is a network that connects devices within a limited geographical area, such as a home, office, school, or campus. Lan can be said
as the network behind your router downstream.
Communication and Resource Sharing: LANs enable devices like computers, printers, servers, and other network-enabled devices to communicate and share resources.
High-Speed Connectivity: LANs provide high-speed data transfer rates within the local network, allowing for fast and efficient communication and resource access.
Localized Administration: LANs are typically administered and managed by a local IT team or network administrator who ensures network security, troubleshooting, and maintenance.
Ethernet Technology: LANs often use Ethernet technology, which defines the rules for transmitting data over the network using Ethernet cables and network switches.
Network Topology: LANs can have various network topologies, such as a star topology, where devices are connected to a central switch or hub, or a bus topology, where devices are connected linearly along a single cable.
LAN Parties and Multiplayer Gaming: LANs have been popular for LAN parties, where individuals bring their computers to a central location and connect them for multiplayer gaming and collaborative activities.
File and Print Sharing: Within a LAN, devices can easily share files, documents, and printers, allowing for efficient collaboration and resource utilization.
WAN (Wide Area Network)
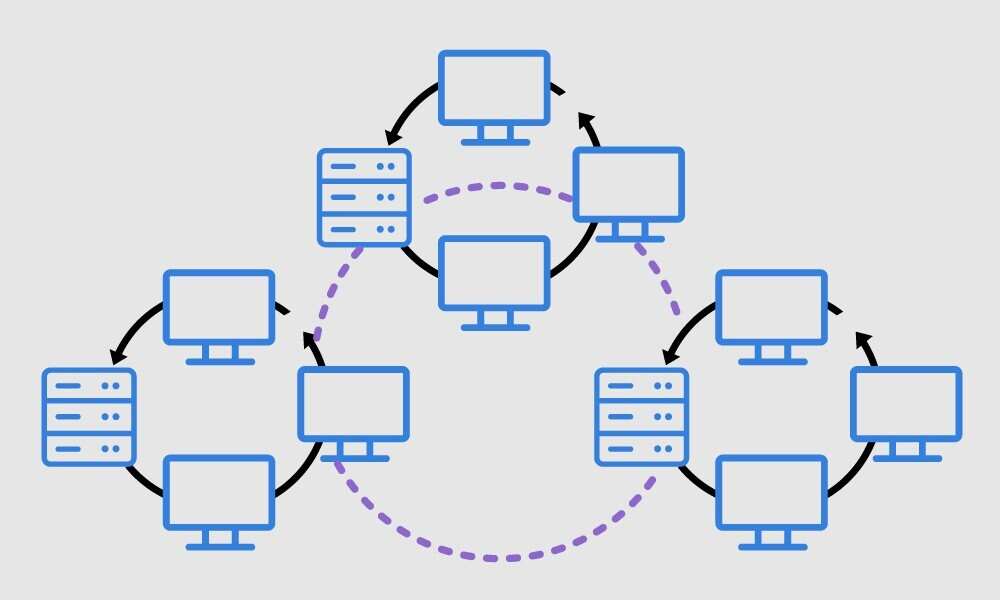
Wide Geographic Coverage: A WAN is a network that spans a larger geographical area, connecting multiple LANs or other networks.
Interconnecting LANs: WANs are designed to connect geographically dispersed LANs, enabling communication and resource sharing between different locations.
Public and Private Networks: WANs can be categorized into public and private networks. Public WANs, such as the Internet, are operated by service providers and accessible to the general public. Private WANs are established by organizations to connect their offices or branches.
Long-Distance Communication: WANs facilitate long-distance data transmission, allowing devices in different locations to communicate as if they were part of the same network.
Data Transmission Technologies: WANs utilize various data transmission technologies, including leased lines, fiber-optic cables, satellite links, and virtual private networks (VPNs), to establish connectivity between different locations.
Internet as a WAN: The Internet itself is the largest example of a public WAN, connecting millions of devices and networks worldwide. It serves as a global infrastructure for data transmission and communication.
Network Protocols
Network protocols are sets of rules and conventions that govern how data is transmitted, received, and processed in a network. They ensure that devices can communicate effectively and understand each other's messages.
Protocols define the format and structure of data packets, including headers, payload, and addressing information. They specify how devices should encapsulate data into packets and how they should interpret and process received packets.
Different protocols serve different purposes, depending on the specific needs of the network and the applications running on it. Some common network protocols include the following:
Transmission Control Protocol (TCP): TCP is a connection-oriented protocol that provides reliable, ordered, and error-checked delivery of data packets. It establishes a connection between two devices, manages flow control and congestion control, and ensures that all packets are received correctly.
User Datagram Protocol (UDP): UDP is a connectionless protocol that provides lightweight and fast transmission of data packets. Unlike TCP, it does not establish a connection and does not guarantee reliable delivery. UDP is commonly used for real-time applications such as streaming media, online gaming, and VoIP.
Internet Protocol (IP): IP is a network-layer protocol responsible for addressing and routing packets across networks. It assigns unique IP addresses to devices, allowing them to send and receive data over the Internet or other networks.
Internet Control Message Protocol (ICMP): ICMP is used for diagnostic and error reporting purposes in IP networks. It provides feedback and error messages related to network connectivity, such as ping requests and responses.
Domain Name System (DNS): DNS is a protocol that translates human-readable domain names into their corresponding IP addresses. It allows users to access websites and services using easy-to-remember domain names instead of numerical IP addresses.
Hypertext Transfer Protocol (HTTP): HTTP is the protocol used for transferring hypertext documents on the World Wide Web. It defines how web browsers and web servers communicate, allowing users to access websites, retrieve web pages, and interact with web applications.
Each protocol has its own set of commands, methods, and procedures that devices follow to communicate and exchange data. These commands and procedures are standardized, enabling interoperability between different devices and software implementations.
Protocols can operate at different layers of the networking model, such as the physical, data link, network, transport, or application layer. The networking model commonly used is the TCP/IP model, which consists of four layers: the network interface layer, internet layer, transport layer, and application layer. Each layer has its own set of protocols.
The network protocols commonly used in the TCP/IP model include Ethernet at the data link layer, IP at the network layer, TCP and UDP at the transport layer, and protocols such as HTTP, FTP, SMTP, and DNS at the application layer.
Understanding network protocols is crucial for network administrators and professionals to configure, troubleshoot, and secure networks effectively. They need to be familiar with the protocols used in their networks, understand their functionalities, and be able to diagnose and resolve issues that may arise.
Protocols are continually evolving and being updated to address new requirements, security vulnerabilities, and technological advancements. New versions and updates of protocols are released to improve performance, enhance security, and support new features and functionalities.
The selection of protocols depends on the specific network requirements, applications, and devices involved in the communication. Different protocols may be used for different purposes within the same network, depending on factors such as bandwidth, latency, security requirements, and the nature of the data being transmitted.
Standardization bodies, such as the Internet Engineering Task Force (IETF) or the Institute of Electrical and Electronics Engineers (IEEE), play a crucial role in developing and maintaining network protocol standards. They define the specifications, protocols, and standards that enable global interoperability and compatibility in networking.
Network protocols also play a vital role in network security. Protocols such as Secure Socket Layer (SSL) and Transport Layer Security (TLS) provide encryption and authentication mechanisms to secure data transmission. Other security protocols, like Internet Protocol Security (IPsec), help protect network traffic at the network layer.
Network protocols are not limited to wired networks but also apply to wireless networks such as Wi-Fi, Bluetooth, and cellular networks. Wireless protocols define how devices establish connections, transmit data, and manage communication in wireless environments.
As technology evolves, new protocols continue to emerge to address emerging needs. For example, protocols like Internet of Things (IoT) protocols (e.g., MQTT, CoAP) are designed to facilitate communication and data exchange between IoT devices.
Modem

A modem stands for "modulator-demodulator" and is a device used to connect a computer or network to an internet service provider (ISP) and establish an internet connection.
Signal Conversion: Modems convert digital signals from computers into analog signals that can be transmitted over traditional telephone lines or cable lines, and vice versa.
Connection Types: Modems come in various types, including dial-up modems (used with telephone lines), cable modems (used with cable TV lines), and DSL modems (used with DSL connections).
ISP Connectivity: Modems connect to the ISP's network infrastructure, allowing users to access the internet and communicate with other devices and networks.
Authentication and Security: Modems often include authentication mechanisms to verify user credentials and establish secure connections with the ISP's network.
Data Transmission Speed: The speed of a modem's data transmission is measured in bits per second (bps), with higher speeds providing faster internet connectivity.
Network Interface Chips (NICs):

NIC also called Network Interface Card is a chip that helps the computer connect to the network, this chip is nowadays preinstalled into the motherboard. When we say we have an ethernet port in our laptop it is NIC.
A network interface chip (NIC) is a small piece of hardware that helps devices, like computers or laptops, connect to computer networks.
It acts as a middleman between a device and the network, allowing them to communicate and share information.
NICs have a physical port, like a plug or connector, that lets the device connect to the network using cables or wireless signals.
They handle the sending and receiving of data between the device and the network, making sure the information gets to where it needs to go.
NICs support different types of networks, like Ethernet (wired) or Wi-Fi (wireless), depending on how devices connect to the network.
NICs come in different shapes and sizes, such as small chips or cards that can be plugged into a computer's expansion slots.
They have a specific speed or data transfer rate, which determines how quickly information can be sent or received between the device and the network.
NICs work with software called drivers, which help the device's operating system understand how to use the NIC and communicate with the network.
Some NICs have extra features, like Quality of Service (QoS), which prioritizes certain types of data for better performance.
Upgrading a NIC can improve a device's network connection, speed up data transfers, or add support for newer network technologies.
Conclusion
In this first part of our networking series, we explored the foundational concepts and technologies that form the basis of modern networking. Understanding these concepts sets the stage for diving deeper into more advanced topics in subsequent parts. Stay tuned as we continue our journey through network protocols, IP addressing, subnetting, and more.
